Social Engineering makes use of PDF for Phishing
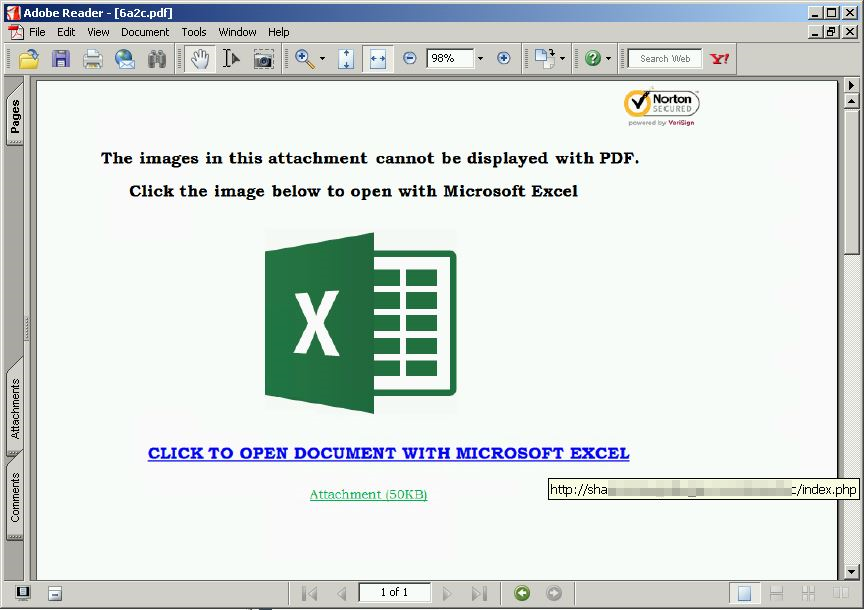
A new variant of the Phishing attack makes the PDF file look like a protected Excel file that can only be displayed with Microsoft Excel after entering email credentials. The attachment is mainly carried by an email message that pretends to be official communication, faking authenticity. It urges the potential victim to open the file by following the link offered in the PDF file. When a user tries to open the attachment, an error message is displayed that instructs the user to “Open document” with Microsoft Excel”. This, in reality, is a link to a website.
For an informed user, an event such as this is enough to raise the alarm since Adobe Reader is used for reading a PDF file, and not an Excel file. Clicking the link opens your browser and lands you on a web page, where the Social Engineering attack continues with a message that the document is protected because it is confidential, and therefore you need to sign in with your email credentials. Why is this social engineering technique used? It involves a human element, so preventing these attacks can be tricky for enterprises. Moreover, it invokes urgency, fear, and other negative emotions in the victim, forcing him to promptly reveal sensitive information by clicking a malicious link or opening a malicious file. Once you enter the information and a cybercriminal has access to your email, he can launch further phishing attacks against your contacts, or gain access to your online banking. Microsoft Edge browser through SmartScreen technology block these phishing pages from loading. So, users using Edge browser for web browsing need not worry. Also, recent versions of the popular browsers such as Mozilla Firefox and Google Chrome are equipped with requisite tools to avoid phishing instances. It is, therefore, advisable to always use the latest release of modern Internet Browsers.
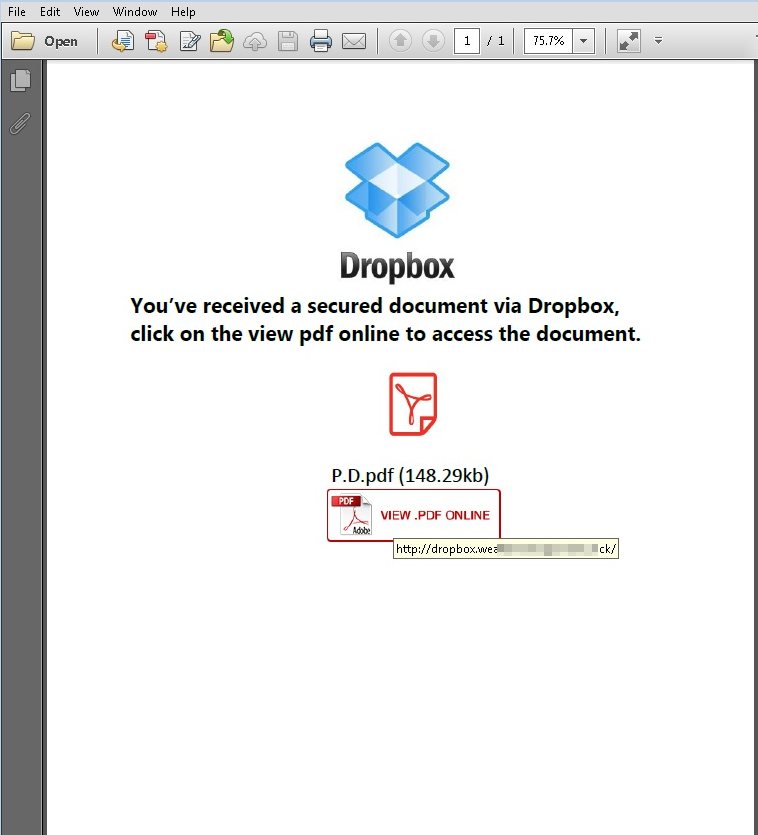
Additionally, Windows Defender can detect and block malicious PDF attachments and other malicious code. The second method involves a slight variation where the PDF urges a user to click on a link that supposedly takes him to an address where he can view a Dropbox-hosted document online. Again, here, the user is redirected to a phishing page that “allows” him to view the document only if he enters his correct email credentials.
Awareness is the key here. You should look for the URL address. If it is using HTTP not HTTPS, it is not a secure session but a well-crafted phishing page. Close the page right away and exit!
How to stay safe from Phishing attacks
Social engineering attacks are designed to take advantage of the fear that leads to possible lapses in decision-making. So, awareness is the key. Never open email attachments or click links in suspicious emails. Also, security features in Windows 10 can help you identify and stop phishing attacks. Read this post for more on how to protect yourself from Social Engineering attacks. Now read: What is Socially Engineered Malware and what precautions can you take?